Contents
Duo Trust Monitor is a threat detection feature focused on surfacing valuable and actionable security events to Duo administrators.
Overview
Duo Trust Monitor helps administrators detect, and respond to, account security threats. It uses machine learning and heuristic models based on known attack patterns like:
- Multi-Factor Authentication Request Generation
- Multi-Factor Authentication Interception
- Adversary-in-the-Middle
- Steal Web Session Cookie
- Modify Authentication Process: Multi-Factor Authentication
In addition to rule-based heuristics, Trust Monitor creates a baseline of normal user and device access behavior by analyzing and modeling Duo authentication data. The feature considers:
- who typically accesses
- which applications
- from which devices
- at what times
- from what locations
- using which authentication methods
Duo scores deviations from this baseline based on their distance from expected behavior. Trust Monitor surfaces highly anomalous access and device registration attempts to highlight potentially suspicious activity and aid in investigations around compromised credentials, account takeover, or application access abuse. Visibility into abnormal access attempts enables Duo administrators to detect suspicious activity and tighten access policies.
Duo's Trust Monitor feature is part of the Duo Premier and Duo Advantage plans.
Video Overview
Trust Monitor Data
Duo Trust Monitor analyzes and models authentication and registration telemetry in order to highlight risk, identify known threat models, and adapt its understanding of normal user behavior. Here is a sampling of some of the telemetry Duo Trust Monitor considers:
| Data Type | Definition or Example |
|---|---|
| User | jsmith |
| Timestamp | Current server timestamp in seconds |
| Application | Cisco AnyConnect VPN, Office 365 |
| Factor | Push, SMS, Passcode |
| IP address of access or auth device | The IPv4 address of the user to be authenticated. |
| Access or authentication device characteristics | Various, pending use of Duo Device Insight, Duo Desktop, and Trusted Endpoints. |
| Authentication result | Granted, Failure, Fraud |
Duo Trust Monitor may leverage up to 180 days worth of historical Duo data to define a baseline. However, organizations don’t need this much data for Duo Trust Monitor to be useful. We recommend customers enable the feature after using Duo in their environment for at least six weeks. Some event types, such as bypass use, user marked fraud, and registration posture, can provide insight sooner.
Upon enabling the feature, Duo Trust Monitor will begin evaluating available authentication and registration data immediately and begin to surface Security Events within 24-48 hours. Duo Trust Monitor on average surfaces two events per day. The surfaced events will have the highest anomaly scores of the cohort analyzed.
Duo Trust Monitor operates on Duo usage data only and does not currently ingest any third-party data to create models of behavior; therefore all data analyzed is currently covered under the Cisco Online Privacy Statement and described in the Cisco Duo Privacy Data Sheet.
Assessing Risk
Duo Trust Monitor uses a variety of tactics to build out a threat model. Duo Trust Monitor evaluates the effect of each component over time and learns which combinations provide the most security value. Here is a sampling of some of the models present within the feature:
| Model | Description |
|---|---|
| Novelty | Presence of a new variable in the access attempt. This includes a brand new device or location, or an attempt to access an application for the first time. |
| Rarity | Rarity covers the cases where a variable isn’t new, but is exceedingly infrequent, such as a variable present in 1% of access attempts. |
| Attack Pattern | Known patterns in the world of access security, such as unrealistic travel logins, device registration, and brute force attacks. Duo Trust Monitor surfaces attempts that fit these patterns. |
| Known Signal | Examples of inherently risky signals include a user marking an attempt as fraud or an admin applying bypass status to a user. |
| Compounding Risk | Access attempts that include more anomalous variables or distinct threat models combine to be more risky than those with fewer. |
| Administrator Designated | Duo Trust Monitor’s Risk Profile enables Duo administrators to set priority assets. These assets are then prioritized in the feature’s risk assessment. |
Risk Profile
We encourage you to designate your organization’s Risk Profile when first setting up Duo Trust Monitor. The Risk Profile flow enables administrators to select a prioritized set of Duo-protected applications, user groups, and locations/IPs.
By setting and saving the Risk Profile, Duo Trust Monitor will weight Security Events involving these selections as more important than anomalies that don’t include a Risk Profile designation. Risk Profile anomalies appear at the top of the Security Events board and they are also marked with a yellow shield icon. Hovering over the yellow shield icon explains the connection between the event and the Risk Profile.
Setting the Risk Profile is required to surface and view events. If an administrator creates a Risk Profile which selects every application, group, and location, Duo Trust Monitor still functions, but the feature will not prioritize any anomalies specifically over others.
Setting up a Risk Profile
Role required: Owner or Administrator
When creating a Risk Profile, you'll step through selecting event properties for inclusion in the profile.
To set up a Risk Profile:
-
Log into the Duo Admin Panel and navigate to Trust Monitor → Risk Profile.
-
Click Create Risk Profile.
-
The first step is selecting applications. Scroll through the list of all applications protected by Duo in your organization’s environment, and select the high-value applications to include in the Risk Profile. We recommend selecting three to five applications.
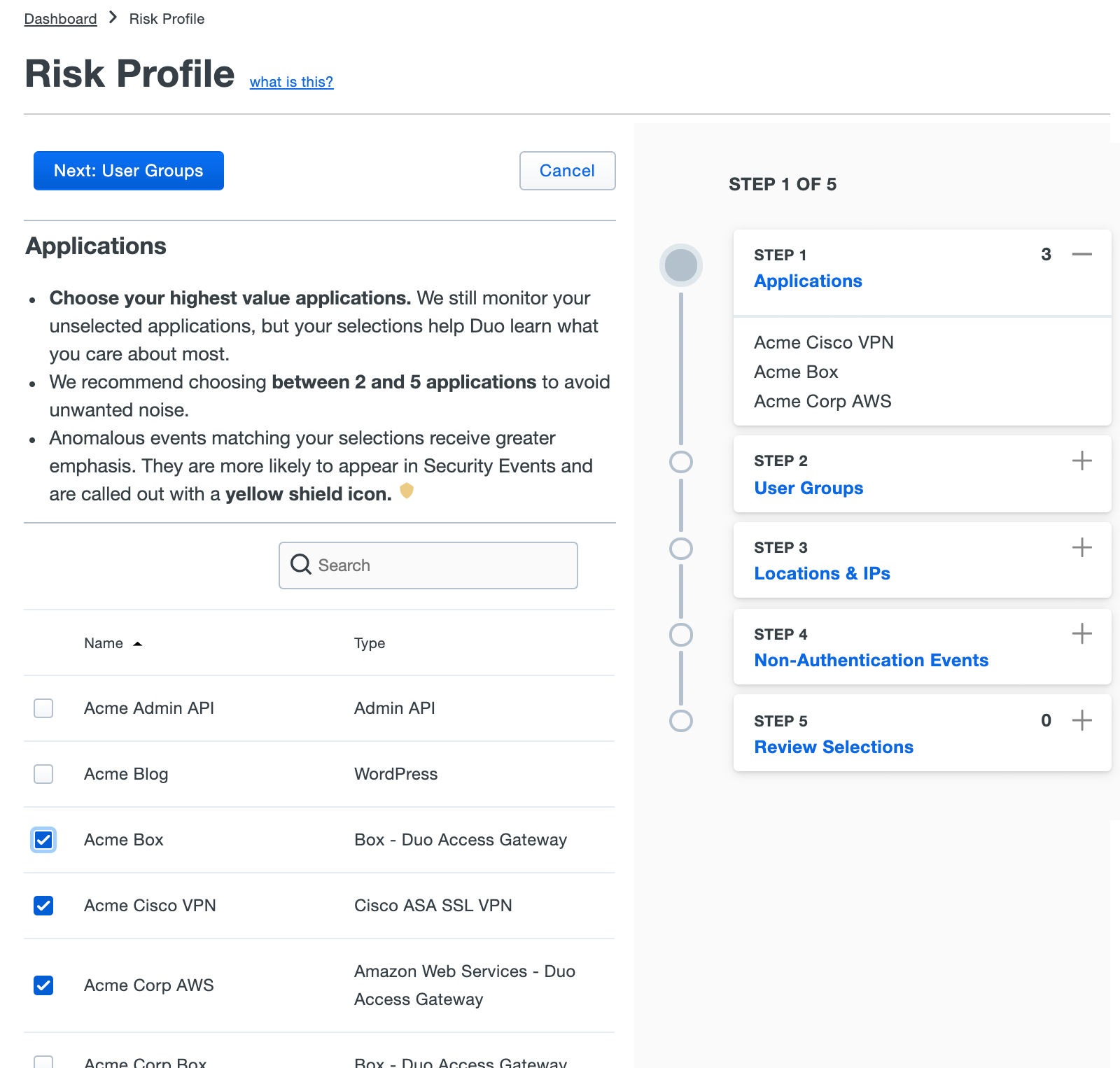
Once you've selected the applications to include, click Next: User Groups.
-
Your next step is selecting the priority user groups. Highly credentialed power users, contractors, and users in bypass mode are often selected, but the exact configuration will vary by organizational structure. We recommend selecting three to eight groups.
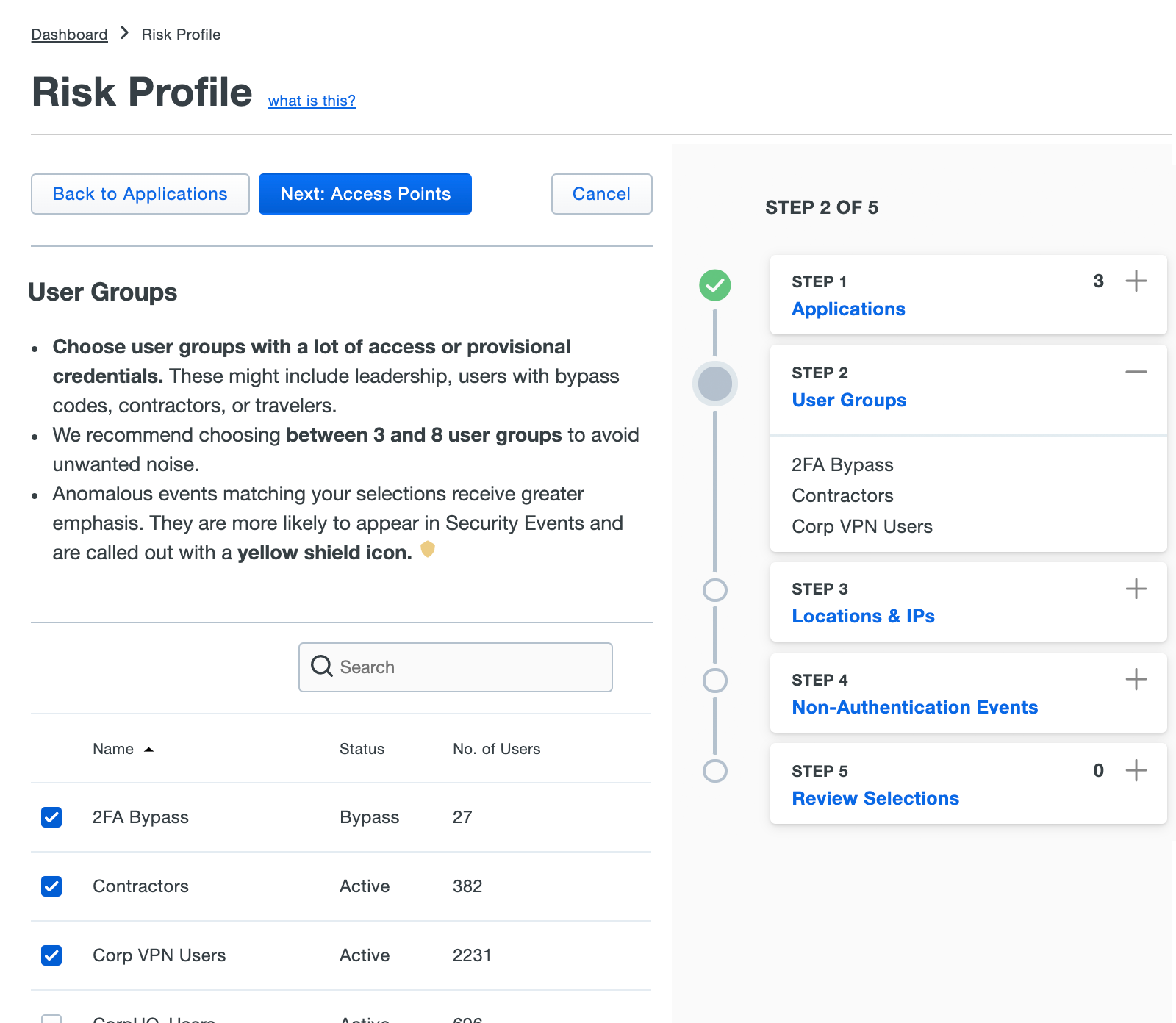
After you've selected priority user groups, click Next: Access Points.
-
In this step of configuring the Risk Profile you set trusted IPs or select risky countries. Typical selections would be countries where your organization doesn’t do any business or have any users, meaning an access attempt from those countries would warrant some suspicion. For low-risk IPs, companies may enter corporate network blocks or trusted IP ranges. To reiterate, this tool merely prioritizes anomalies; events from a trusted network or country can still be surfaced in the Security Events dashboard.
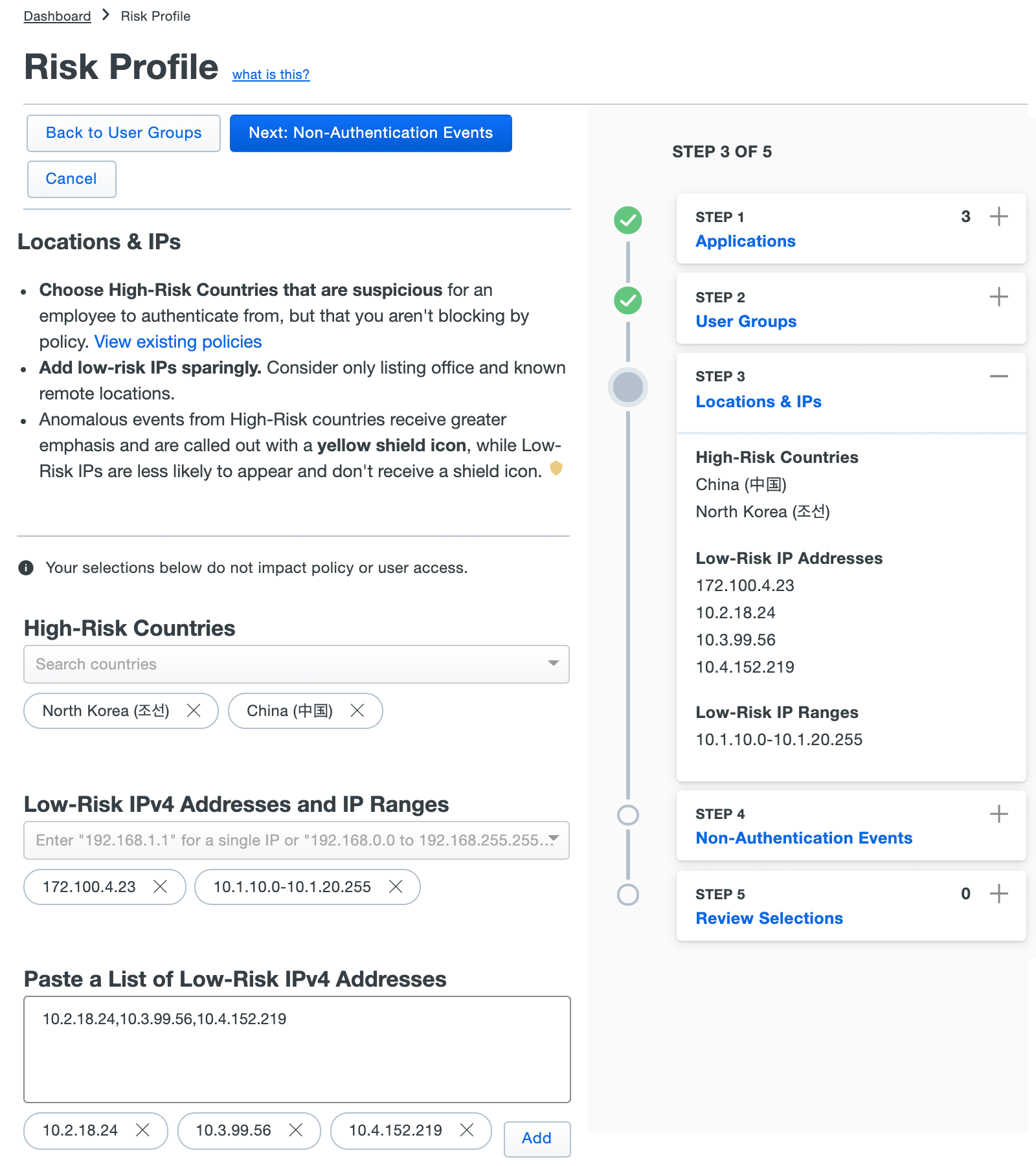
Make your location and IP selections, and then click Next: Non-Authentication Events.
-
If you want Trust Monitor to surface non-authentication events that may be considered high-risk, like when a Duo admin applies bypass status to a user, enable that in this step.
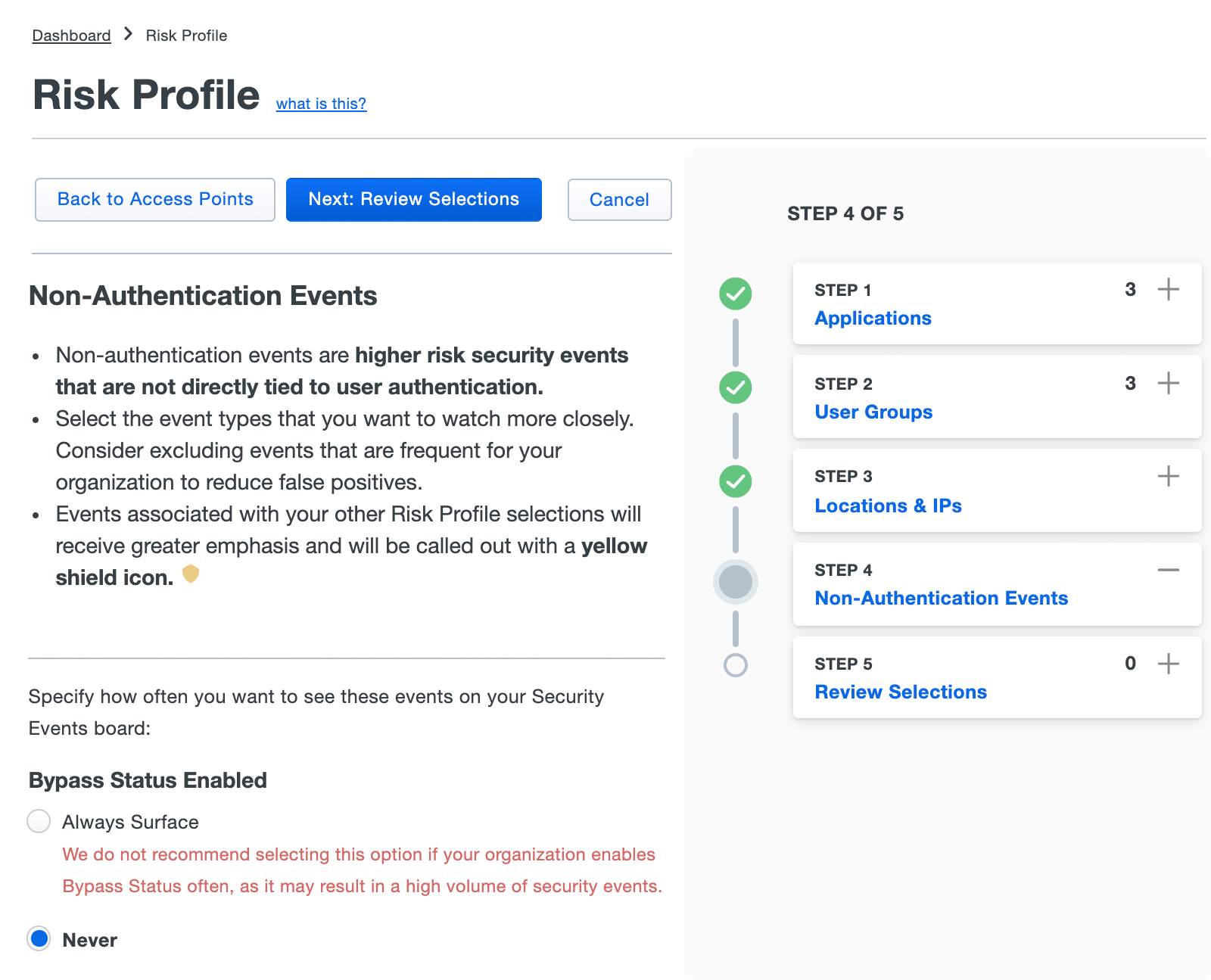
Click Next: Review Selections to move on to the final step.
-
Review your application, group, location/IP, and non-authentication event selections. If you need to make corrections you can use the "Back to ..." buttons to revisit each of the selection steps. If everything looks OK, click Apply Configuration.
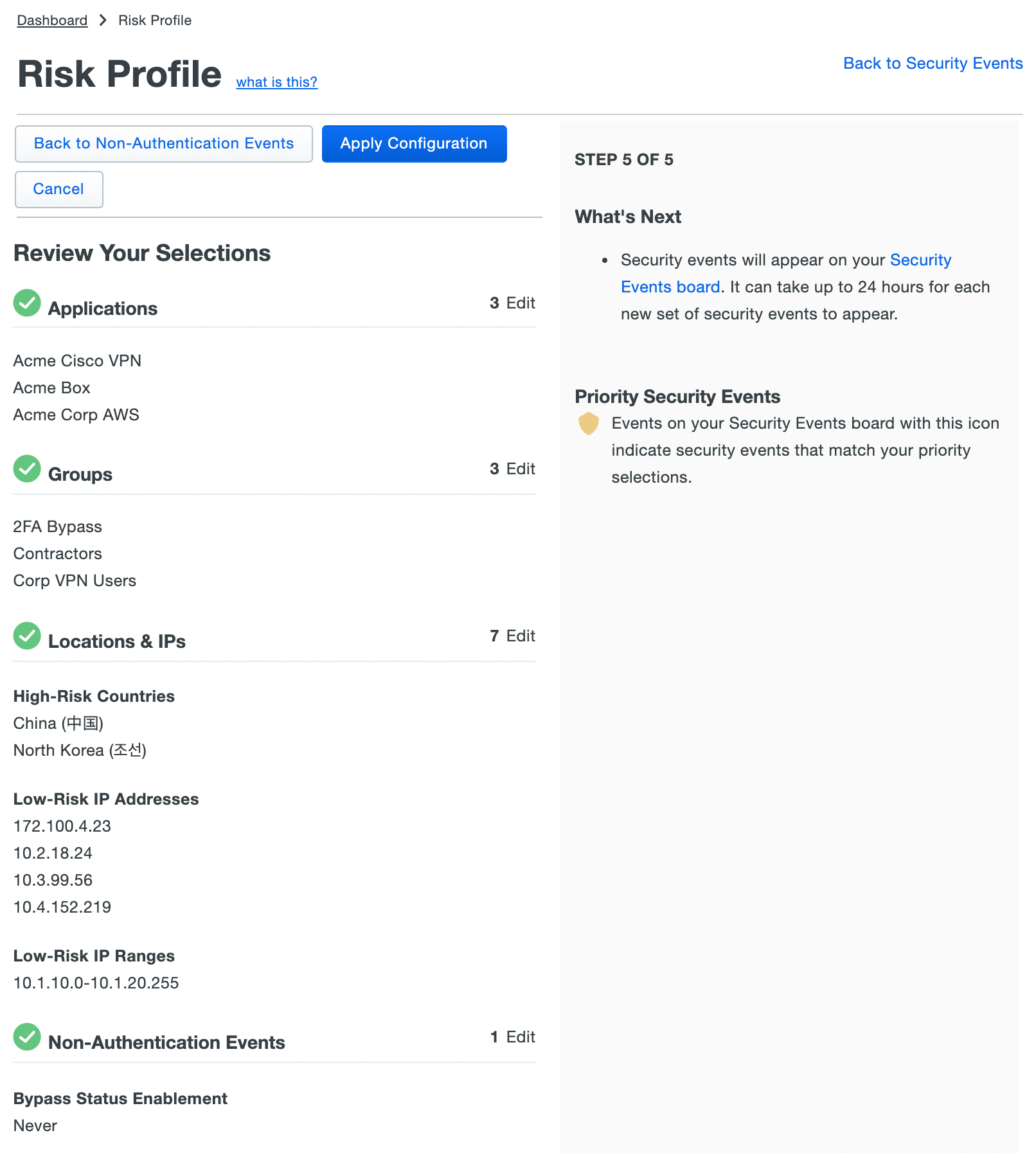
Once you apply the new Risk Profile, Duo Trust Monitor starts prioritizing events based on your selections and makes them visible on the Security Events board.
Editing an Existing Risk Profile
Role required: Owner or Administrator
If something within the organization changes, you can always edit your Risk Profile to reflect the change.
To edit the Risk Profile:
-
Navigate to Trust Monitor in the Duo Admin Panel.
-
Click the Edit Risk Profile link on the right side of the Security Events board.
-
Repeat stepping through the Risk Profile selections, modifying the settings as needed.
-
Click Apply Configuration to save your edits to the Risk Profile.
After the edit, Duo Trust Monitor will prioritize and mark events based on the new Risk Profile.
Security Events
Role required: Owner or Administrator to triage events; Read-only admins may review events.
Security Event Information
The Security Events dashboard is where you can review the events surfaced by Duo Trust Monitor. A Security Event is an authentication or registration that surfaced due to its anomaly score, known attack patterns, or other heuristics (i.e. the Risk Profile designation, etc.). The top events represent the highest priority event at any given time, based on both anomalistic nature and Risk Profile weighting.
You may not see any security events in the table when you first access it. That means that the majority of your users don’t have enough authentications to build accurate modeling. As they continue to use Duo we will automatically evaluate and begin providing events when the authentications increase. It’s important to note that, if you have set your log retention to anything under 90 days, you will not be eligible for Machine Learning modeling and will only see security events for registration events, bypass status (if enabled in your Risk Profile), and user marked fraud. Duo recommends retaining at least 180 days of logs to build the most accurate Trust Monitor models.
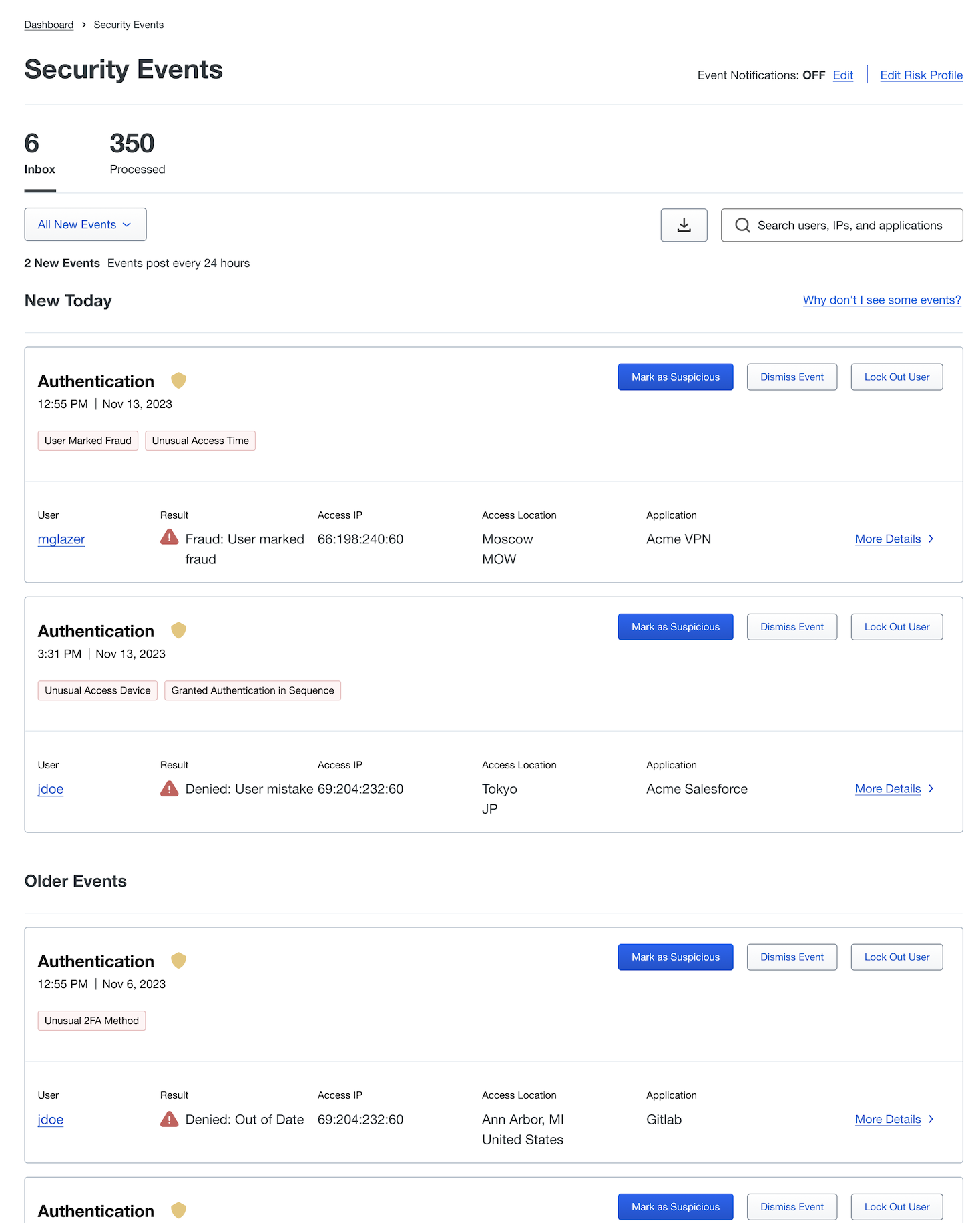
Each event includes a variety of informational content:
-
The event type, e.g. "Authentication" or or “Device Registration”. If an event shows a yellow shield icon, it is related to a Risk Profile designation. Hovering over the shield will show how the event connects to the Risk Profile.
-
The time and date of the event.
-
The reasons for surfacing the event, shown as red bubbles. Hover over the bubble to view more context behind the cause. For example, in the case of a new access device, additional information shows recent devices used in access attempts and their relative frequency - highlighting the rarity or novelty of the device used in the Security Event.
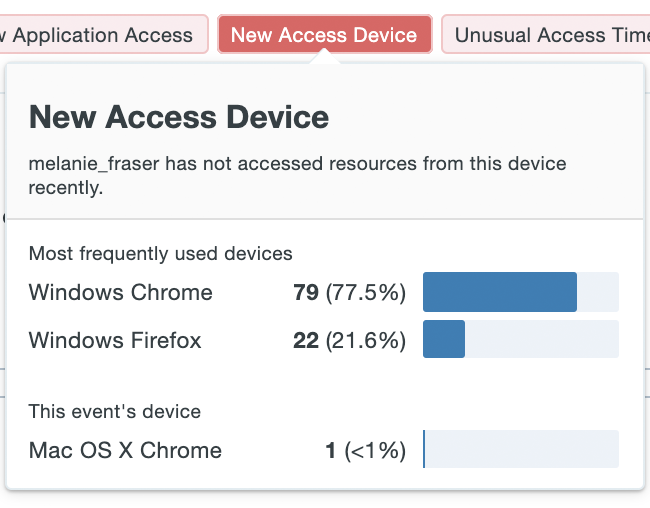
Some potential causes that could be surfaced by Duo Trust Monitor:
Cause Description New Access Device The user has not used this device in the last 180 days. New Access Device IP The user has not logged in from this IP address in the last 180 days. New Application Access The user has not accessed this application in the last 180 days New Location The user has not accessed from this location in the last 180 days Unrealistic Travel The time and distance between two distinct logins makes it impossible for the user to have made both attempts. Unusual Access Device IP The user has infrequently logged in from this IP address in the last 180 days. Unusual 2FA Method The user infrequently accesses applications utilizing this 2FA method. Unusual Application The user infrequently accessed this application in the last 180 days Unusual Time The user infrequently accesses applications at this time of day. User Marked Fraud The user marked the authentication attempt as fraud. Granted Authentication in Sequence The sequence of anomalous events contains successful authentications. Insecure Device Property The registration event contains a device with insecure properties. Dormant User The registration event occurred on a dormant user account. -
User: The Duo username.
-
Result: The outcome of the authentication event.
-
Access IP: The IP address of the accessing device. IP addresses associated with a known public VPN or TOR network will be tagged accordingly in the security event details.
-
Access Location: The geographic location of the access device, as determined by the IP address.
-
Application: The name of the Duo-protected application accessed.
-
More Details: Click this link to view more detailed information and additional context regarding the access attempt and a timeline of access events surrounding the surfaced anomalistic event.
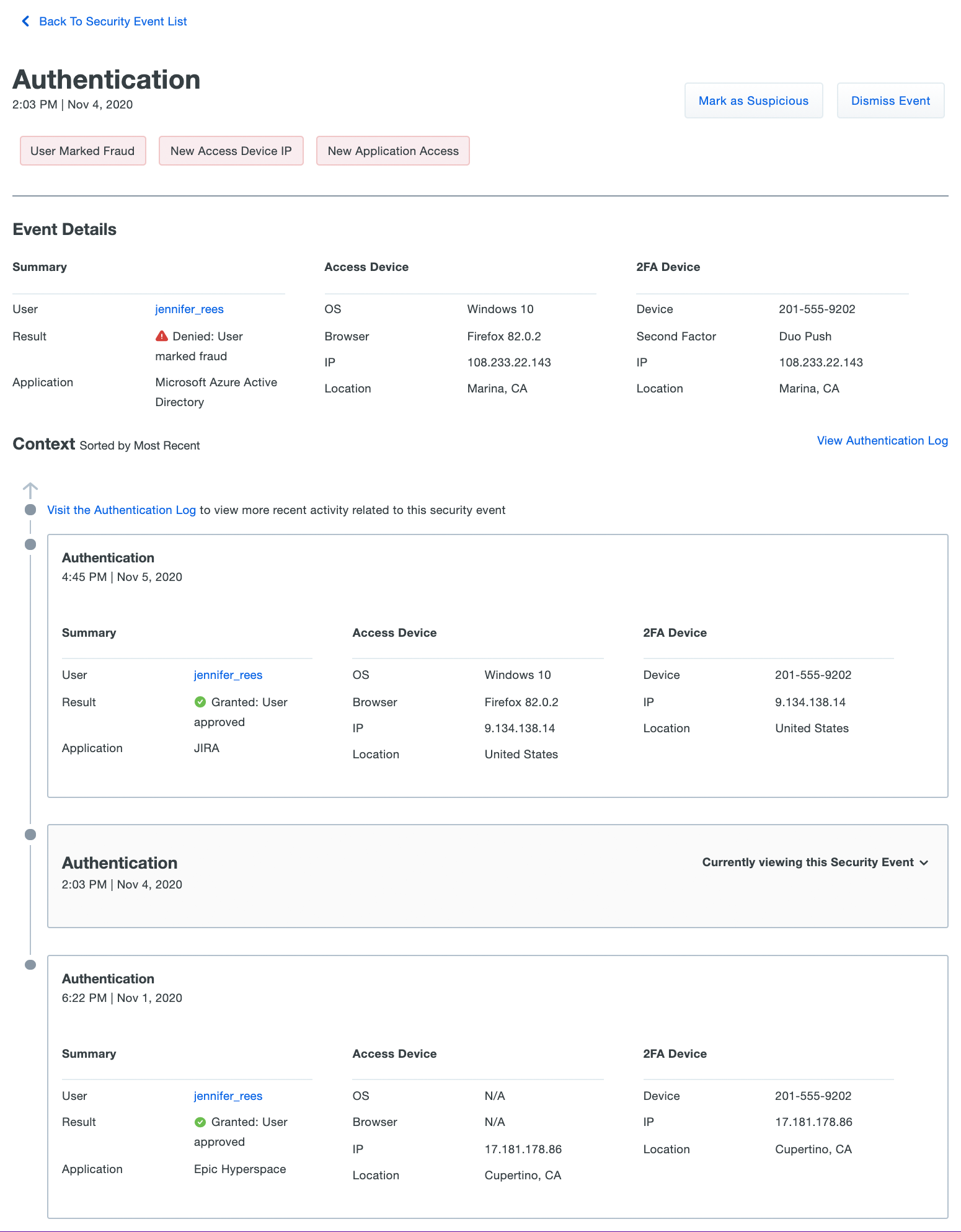
Processing Security Events
Process the new anomalous events by choosing a response, clicking Mark as Suspicious, Dismiss Event, or Lock out user from the security events dashboard or from the details of an individual event. When you process an event you'll be able to provide optional feedback as to why the event was suspicious or uninteresting, which will help the Duo Trust Monitor data science team improve the model going forward.
Click Mark as Suspicious to process Security Events. Marking an event as suspicious helps Duo Trust Monitor data science improve model precision by adapting its understanding of what constitutes normal behavior for a user. You can provide optional feedback about why the event was suspicious, or leave comments regarding the event, especially useful in cases where you or another Duo administrator connected with the user regarding the access attempt.
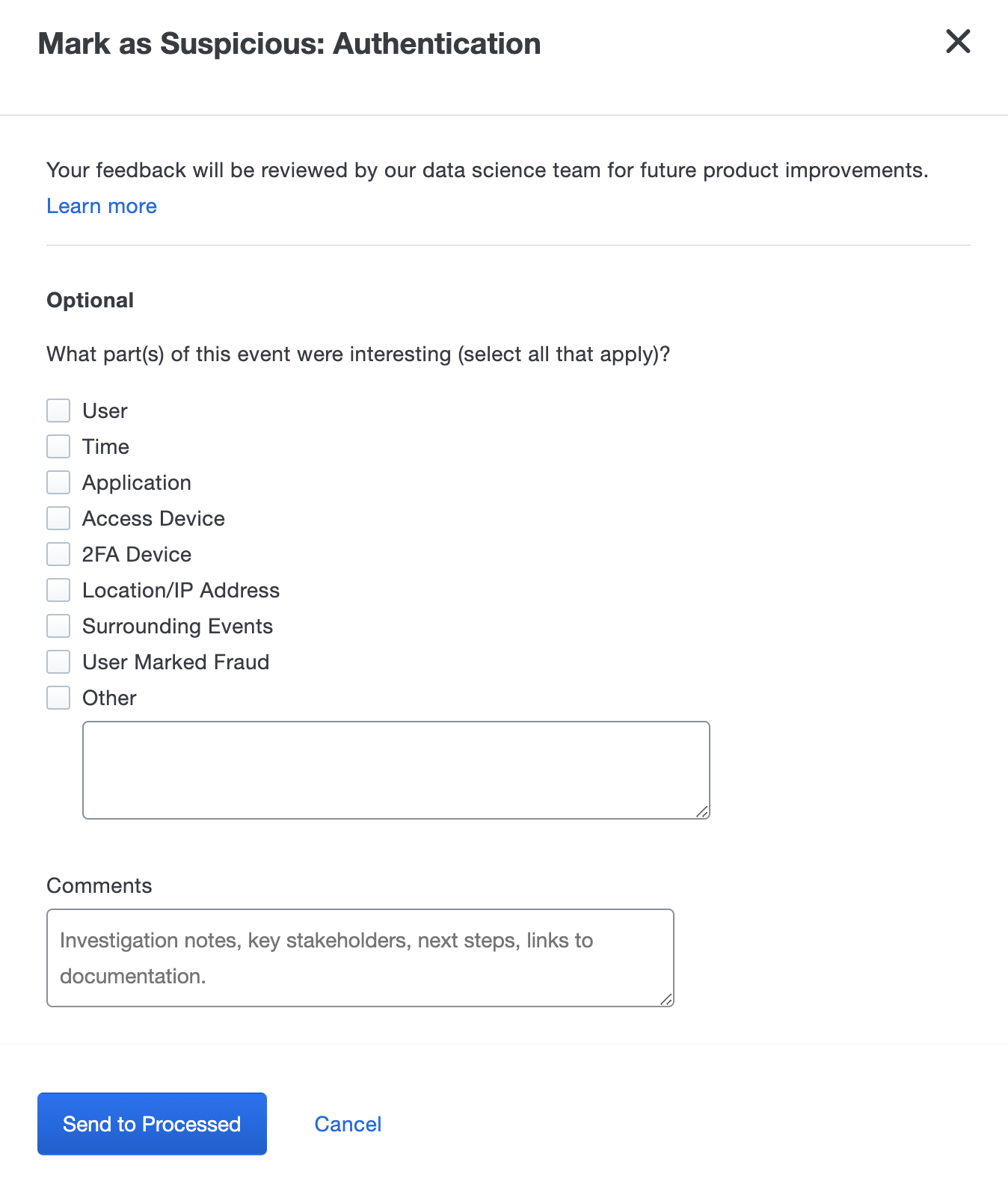
When finished entering your feedback and comments, click Send to Processed to move the event into the "Processed" tab on the Security Events dashboard. Processed event details and comments can be reviewed here in the future.
Note: At this point, Duo Trust Monitor is a self-contained tool and there is no automated workflow to remediate an event outside of the Duo Admin Panel.
Click Dismiss Event to respond to benign or unsuspicious access events surfaced by Duo Trust Monitor. Dismissing an event helps Duo Trust Monitor improve model precision by adapting its understanding of what constitutes normal behavior for a user. As with suspicious events, you can provide additional feedback or comments about why the event was uninteresting.
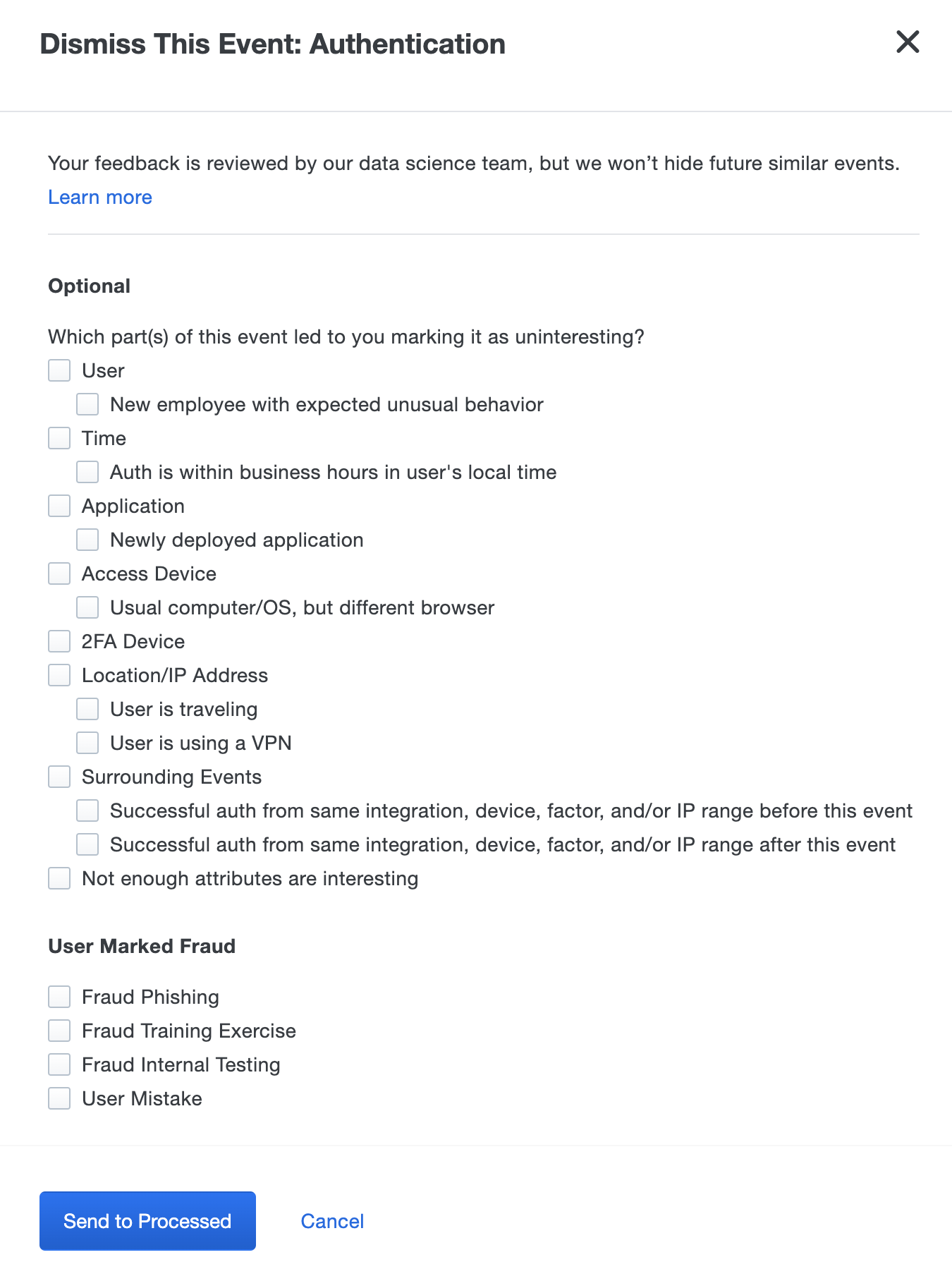
Click Lock out user when the suspicious activity of a user warrants the restriction of access to Duo MFA protected resources.
The user status changes to "locked out" and session cookies for those resources will be redacted.
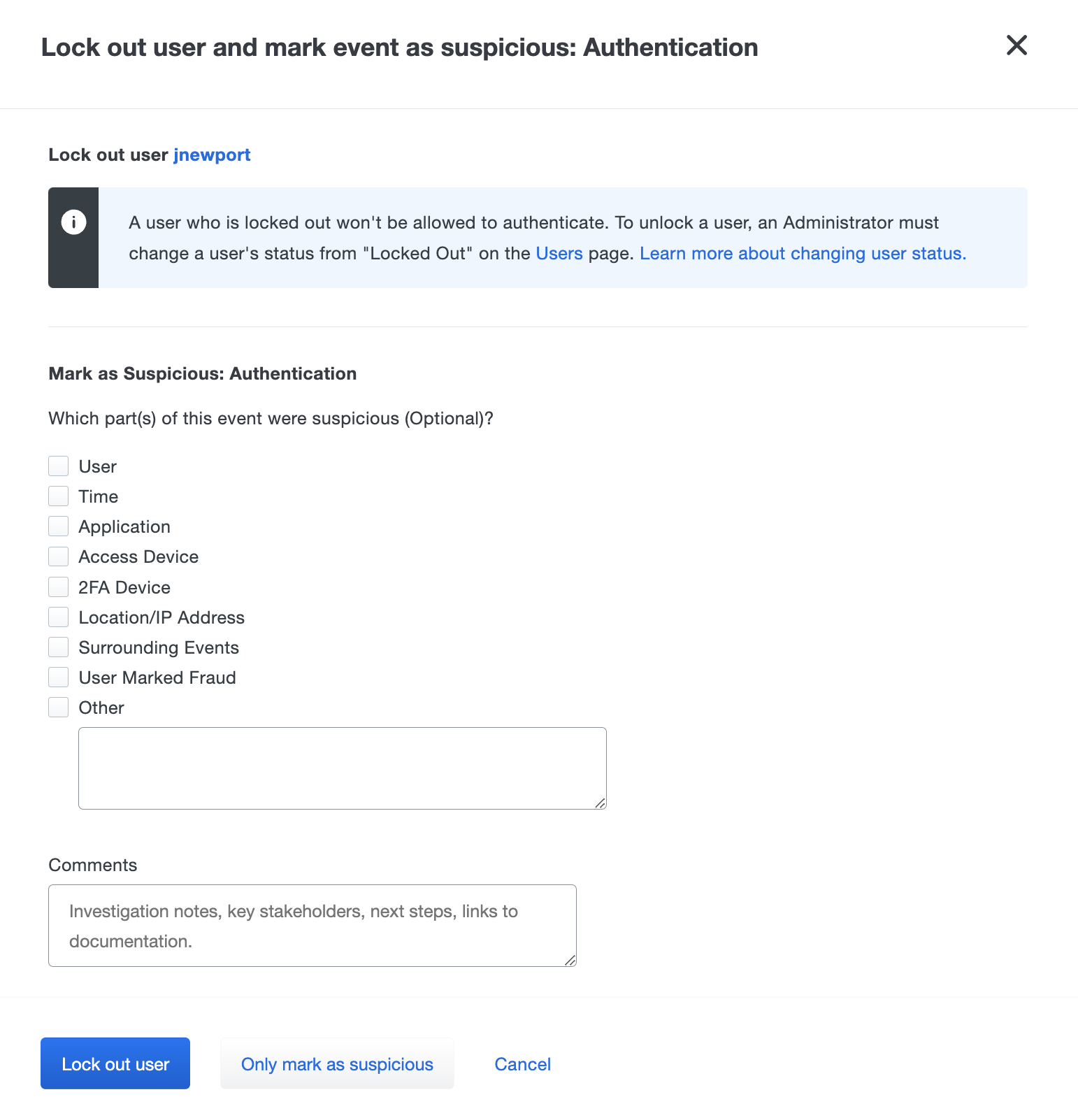
Administrators with appropriate permission can change the user's status from "Locked out" to "Active" or "Bypass" from the user's details page to allow the user back into applications.
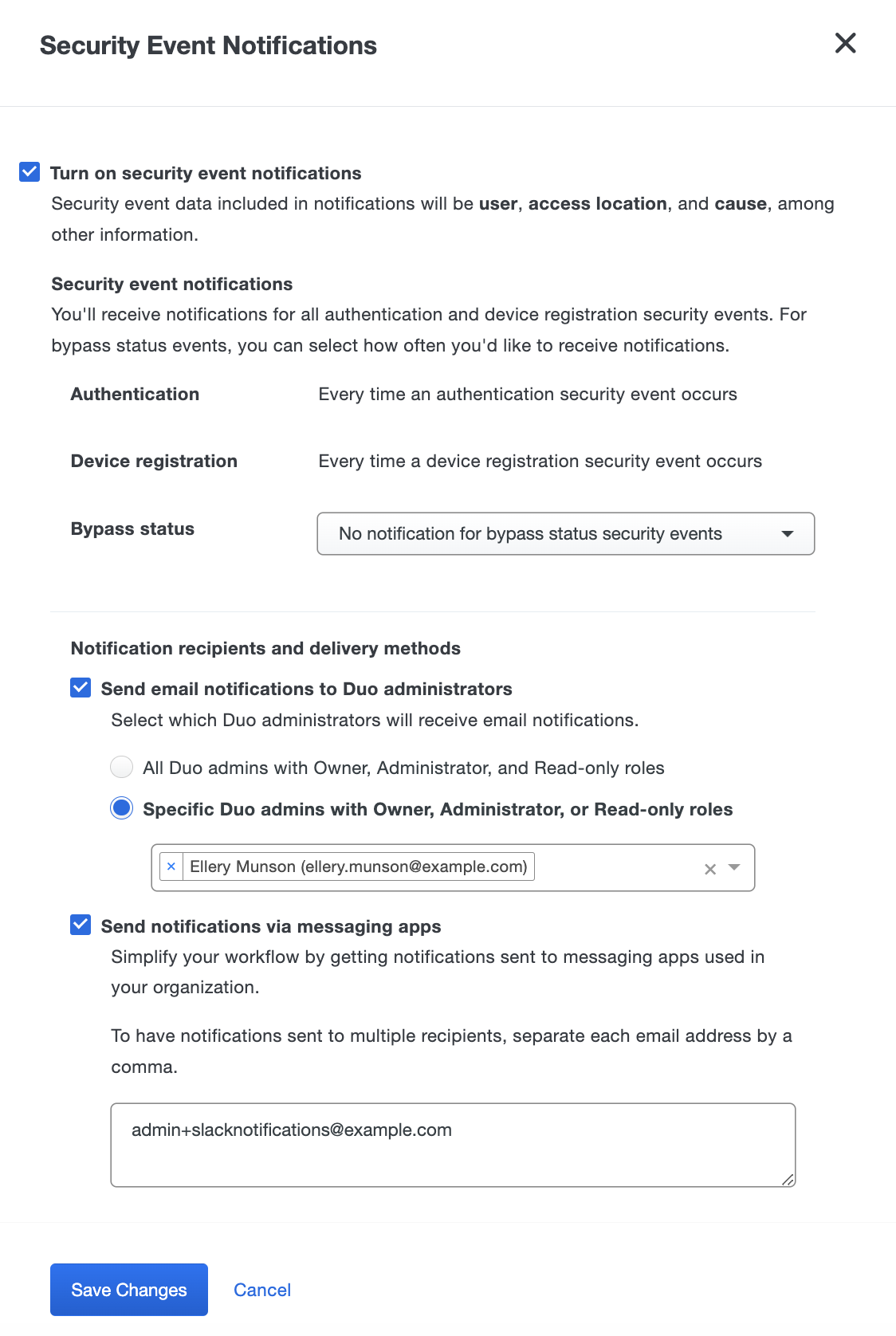
Security Event Notifications
Role required: Owner or Administrator
Security Event notifications allow you to be aware of new security events, without having to log into the Duo Admin Panel, by sending email notifications. These notifications include the same information you would see for the security event in the Security Events dashboard.
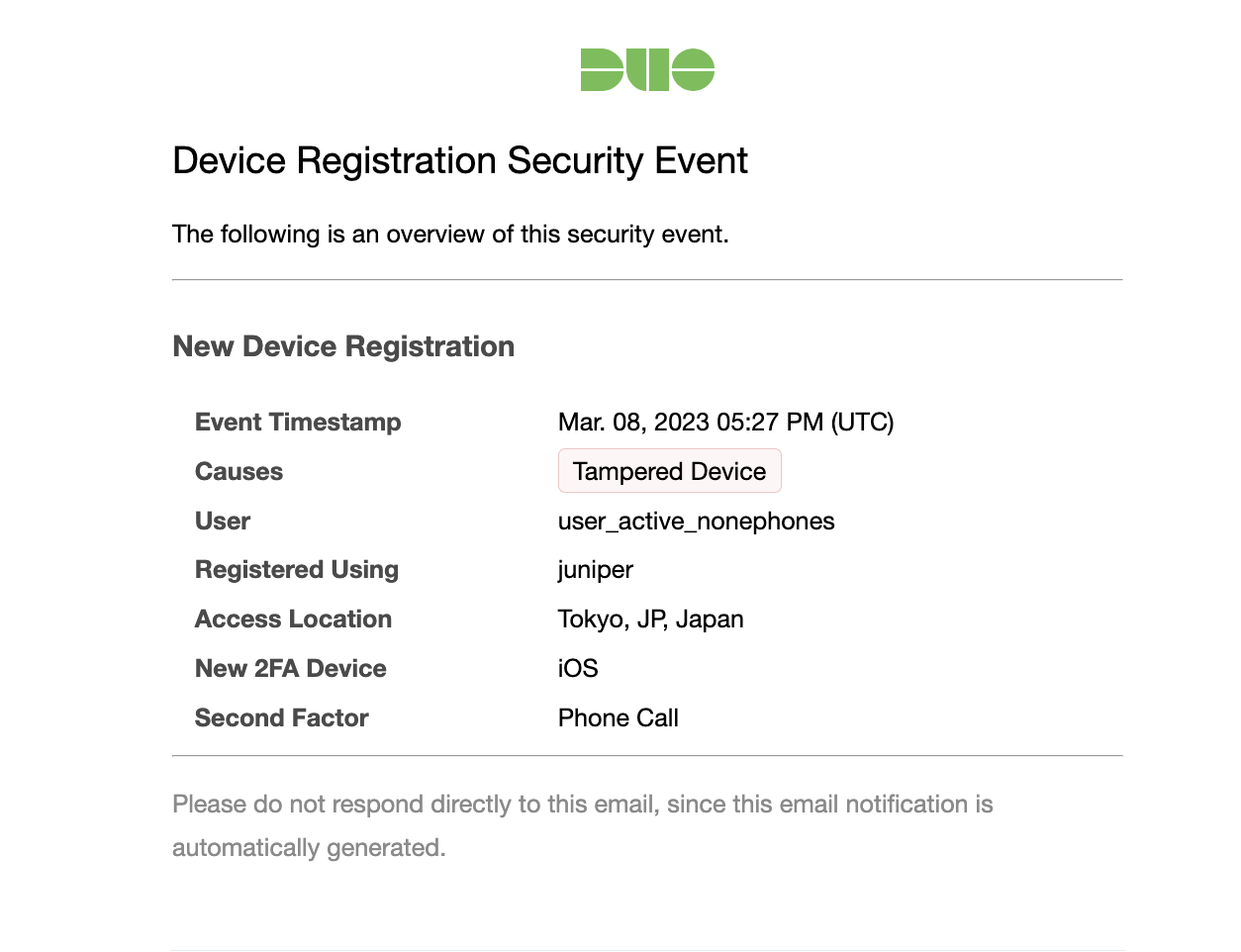
To enable Security Event notifications:
-
Log into the Duo Admin Panel and navigate to Trust Monitor → Security Events.
-
Click the Edit button next to "Event Notifications" on the top right corner of the page.
-
Enable notifications by the checking the box next to Turn on security event notifications. The default options send an email notification for each security event surfaced by Trust Monitor.
-
You can opt out of bypass status security email notifications by selecting No notification for bypass status security events from the Bypass status drop-down list.
If you did not enable surfacing bypass status events when configuring your Risk Profile, then you won’t receive email notifications for these events.
-
To send emails notifications to Duo administrators, check the box next to Send email notifications to Duo administrators. Choose one of the following options for email notifications:
- All Duo admins with Owner, Administrator, and Read-only roles: Duo administrators with the Owner, Administrator, and Read-only role will be sent an email for every security event.
- Specific Duo admins with Owner, Administrator, or Read-only roles: Select specific Duo admins from the drop-down to receive security event email notifications.
-
To send emails notifications to custom email addresses, check the box next to Send notifications via messaging apps. Enter in the emails you want to receive notifications into the text box, separate each email by a comma.
-
Click Save Changes.
Trust Monitor API
Use the Trust Monitor Admin API endpoint to retrieve Duo Trust Monitor Security Events.
Troubleshooting
Need some help? Try searching our Knowledge Base articles or Community discussions. For further assistance, contact Support.
All Duo customers have access to Level Up, our online learning platform offering courses on a variety of Duo administration topics. To access Level Up content, sign in with the same email address you use to sign in to the Duo Admin Panel.
