Documentation
Duo Trusted Endpoints - Microsoft Intune Managed Endpoint Device Deployment
Last Updated: May 16th, 2024Contents
Certificate-based Trusted Endpoint verification for Intune will reach end-of-life in a future release. Migrate existing iOS Certificate Configuration management integrations to iOS Configuration and existing Windows Certificate Configuration management integrations to Windows Configuration. Learn more about the end-of-life timeline and migration options in the Duo Trusted Endpoints Certificate Migration Guide.
Duo's Trusted Endpoints feature secures your sensitive applications by ensuring that only known devices can access Duo protected services. When a user authenticates via the Duo Prompt, we'll check for the access device's management status. You can monitor access to your applications from trusted and untrusted devices, and optionally block access from devices not trusted by your organization.
Trusted Endpoints is part of the Duo Essentials, Duo Advantage, and Duo Premier plans.
Before enabling the Trusted Endpoints policy on your applications, you'll need to deploy the Duo device certificate or REST API access for Duo to your managed devices. This guide walks you through Intune configuration for Android and iOS mobile devices and Windows endpoints.
Mobile Trusted Endpoints and Verified Duo Push: Trusted endpoint verification of iOS and Android devices with Duo Mobile uses the standard Duo Push approval process and will not prompt for a Duo Push verification code, even if the effective authentication methods policy for the user and application has "Verified Duo Push" enabled.
Prerequisites
- Access to the Duo Admin Panel as an administrator with the Owner, Administrator, or Application Manager Duo administrative role.
- Access to Microsoft Entra ID as an administrator with the rights to create new app registrations.
- An Azure Subscription associated with your Microsoft Entra ID tenant.
- Intune licensing.
- If configuring for iOS devices, that an Apple MDM Push Certificate has been configured in Intune and is active.
- Deploy Duo Desktop to the Windows clients for which you want to verify management status.
Microsoft Entra ID Configuration
Perform these Azure app registration steps prior to the specific Android, iOS, or Windows configuration steps. You only need to register one Azure app for Duo to use with all three client operating systems. These instructions create a single-tenant application where the application is intended to run within only one organization.
Create Microsoft Entra ID Application
-
Log in to the Microsoft Azure Administrator console as an Azure AD administrator with the "Global Administrator" role.
-
Select the Microsoft Entra ID option from the search.
-
In the Azure portal, navigate to Microsoft Entra ID → App Registrations → New registration.
-
Click + New registration.
-
Enter a descriptive name for the application and select Accounts in this organizational directory only under "Supported account types".
-
Click Register. You'll be sent to the details page for the new app registration.
-
On the newly-created application's page, click API Permissions in the "Manage" section, and then click + Add a Permission.
-
On the "Request API Permissions" page, select Microsoft Graph from the available Microsoft APIs, and then select Application Permissions.
-
Select the following Microsoft Graph permission:
- DeviceManagementManagedDevices.Read.All
-
Click Add Permissions after selecting the Graph permission.
-
Back on the API permissions page you should see the list of API permissions you selected. Click the Grant admin consent for <your Azure domain name> button, and when asked if you want to grant consent for all accounts in your Azure domain click Yes.
Create an Application Secret
-
In the Azure portal, return to Microsoft Entra ID.
-
Click on App registrations in the "Manage" section of your Microsoft Entra ID domain's blade and select the Duo app registration you created earlier.
-
Click Certificates and Secrets in the "Manage" section.
-
Under "Client secrets" click + New client secret. In the Description leave a comment, then under "Expires" select 730 days (24 months) (the permitted maximum). This creates a new secret, but the secret value is hidden until you save your changes. Click Add.
-
The new secret's value is shown after you save. Do not leave or close this page! You will need to copy the secret VALUE (not the "Secret ID") from this page and paste it into your Intune management integration configuration page in the Duo Admin Panel once you create the management integration in the next set of steps below for your OS platform.
This is your only chance to view the secret value! If you leave this area of the Azure portal before entering the secret Intune management integration configuration in the Duo Admin Panel, then you can't view the same key's value again and you'll have to create a new one.
It's a good idea to save this Azure secret in a secure password manager in case you need it again after you finish setting up your Intune management integration, like if you want to add support for other OS platforms in the future.
Android Configuration
Duo determines trusted device status on Android devices by leveraging the installed and activated managed Duo Mobile application on a given device to verify device information.
Use the following instructions to complete setup of your Duo Intune management integration for Android devices.
Create the Intune Integration
- Log in to the Duo Admin Panel and navigate to Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Intune in the list of "Device Management Tools" and click the Add this integration selector.
- Choose Android from the "Recommended" options, and then click the Add button.
The new Intune integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Please note that this integration takes advantage of managed app configuration and therefore Duo Mobile must be installed by your MDM for the device to be considered trusted.
Keep the Duo Admin Panel open in your browser while you access the Azure portal in a new window or tab. You'll need to return to the Intune management integration page to complete the Android configuration steps.
Register Azure Application for Android in Duo
-
In the Azure portal, navigate to Microsoft Entra ID → App Registrations, and then select the Duo app registration you created earlier.
-
Scroll down on the configuration page for your Intune Trusted Endpoints management integration to the "Register Azure Application with Duo" section.
-
Copy the Azure application client secret value that you created during the Azure configuration steps, and paste the copied secret as the Azure Secret value in the third step on your Intune management integration's config page in the Duo Admin Panel.
-
Click Overview on the Duo Azure app registration's page. You'll see the Application (client) ID and Directory (tenant) ID listed at the top of the page.
-
Copy the Application (client) ID value from Azure and paste it as the Azure Application ID value in step 4 on your Intune management integration's config page in the Duo Admin Panel.
-
Copy the Directory (tenant) ID value from Azure and paste it as the Azure Directory ID value in step 4 on your Intune management integration's config page in the Duo Admin Panel.
-
Click Test Configuration to verify Azure API access, and if successful click Save & Configure on the Duo Intune management integration page.
Setup Managed Google Play
-
In the Azure Portal, navigate to Intune → Devices → Enrollment and then select the Android tab.
-
Select Manage Google Play in the "Prerequisites" section to connect to your organization's Google Play account.
-
Grant Microsoft permission to send user/device information to Google, and click the Launch Google to connect now button to access Google.
-
Sign in to Google using the account you use to manage and publish apps in Google Play and complete linking your managed Google Play account to Intune.
Approve Duo in the Managed Google Play Store
-
In the Azure Portal, navigate to Intune → Client Apps → Apps → Android.
-
Click the +Add button and select Managed Google Play in the "App Type" drop-down. The managed Google Play Store opens.
-
Search the Google Play Store for Duo Mobile and click the Duo Mobile app icon to select it from the search results.
-
Click the Select button on the Duo Mobile app page, and click Approve again after reviewing the requested app permissions.
-
When asked "how to handle new app permission requests", select Keep approved when app requests new permissions and then click Done.
-
After you've approved the Duo Mobile app in the Play store, return the Intune Managed Google Play page and click the Sync button.
Configure Managed Duo Mobile
-
In the Azure Portal, navigate to Intune → Apps → App configuration policies.
-
Click the Add button and select Managed devices.
-
Enter the following information on the "Create app configuration policy" page's "Basics" tab:
Name Enter a descriptive name. Description Enter additional information about this new policy, if desired. Device Enrollment Type Select Managed Devices. Platform Select Android Enterprise. Profile Select Personally/Corporate-Owned Work Profile only. -
Click the Select app link next to "Targeted app".
-
In the "Associated App" search find and and choose Duo Mobile. Click OK to return to the "Basics" tab, and then click Next.
-
On the "Settings" tab, under "Configuration settings format", choose Use configuration designer.
-
Click Add+ and select Trusted Endpoint Identifier and Trusted Endpoints Configuration Key. The Trusted Endpoint Identifier should have value type "Variable" and Trusted Endpoints Configuration Key should have value type "String".
-
Return to your Intune management integration page in the Duo Admin Panel and copy the information for these fields from Duo and paste into the corresponding configuration value fields in the Azure configuration designer:
- Trusted Endpoint Identifier
- Trusted Endpoints Configuration Key
Click Next after entering the information for those two configuration settings.
-
On the "Assignment" tab, choose the Azure group to which you would like to push Duo Mobile. We recommend starting with a test group. Click Next after selecting your target groups.
-
Verify the information on the "Review + Create" tab, and click Create if it looks correct.
Assign Duo Mobile to Android Phones
-
In the Azure Portal, navigate to Intune → Apps → All Apps.
-
Select the Duo Mobile app with type "Managed Google Play store app".
-
Select Assignments and then click Add Group.
-
Make the following selections:
- Assignment Type: choose Required.
- Group: choose the Azure group to which you would like to push Duo Mobile. We recommend starting with a test group.
-
Click OK and then click Save.
Duo Mobile should now be available to download from the Intune Work Profile App Store on Android devices.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
Verify Android Device Information with Search
After you configure the connection between Intune and Duo you can verify that a given device's information is being pulled into Duo by searching for the device identifier from the Duo Admin Panel. See Search for Device Identifiers to learn how.
iOS Configuration
Duo determines trusted device status on iOS devices by leveraging the installed and activated managed Duo Mobile application on a given device to verify device information.
Use the following instructions to complete setup of your Duo Intune management integration for iOS devices.
Create the Intune with App Config Integration
- Log in to the Duo Admin Panel and navigate to Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Intune in the list of "Device Management Tools" and click the Add this integration selector.
- Choose iOS from the "Recommended" options, and then click the Add button.
The new Intune with App Config integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Please note that this integration takes advantage of managed app configuration and therefore Duo Mobile must be installed by your MDM for the device to be considered trusted.
Keep the Duo Admin Panel open in your browser. You'll need to refer back to the Intune with App Config management integration page to complete the configuration steps.
Register Azure Application for iOS in Duo
-
In the Azure portal, navigate to Microsoft Entra ID → App Registrations, and then select the Duo app registration you created earlier.
-
Scroll down on the configuration page for your Intune with App Config Trusted Endpoints management integration to the "Register Azure Application with Duo" section.
-
Copy the Azure application client secret value that you created during the Azure configuration steps, and paste the copied secret as the Azure Secret value in the third step on your Intune management integration's config page in the Duo Admin Panel.
-
Click Overview on the Duo Azure app registration's page. You'll see the Application (client) ID and Directory (tenant) ID listed at the top of the page.
-
Copy the Application (client) ID value from Azure and paste it as the Azure Application ID value in step 4 on your Intune management integration's config page in the Duo Admin Panel.
-
Copy the Directory (tenant) ID value from Azure and paste it as the Azure Directory ID value in step 4 on your Intune management integration's config page in the Duo Admin Panel.
-
Click Test Configuration to verify Azure API access, and if successful click Save & Configure on the Duo Intune with App Config management integration page.
Approve Duo in the App Store
-
In the Azure portal, navigate to Intune → Client Apps → Apps → iOS.
-
Click the +Add button and select iOS store app in the "App Type" drop-down.
-
Click on Search the App Store, and type Duo Mobile in the app search bar.
-
Click on Duo Mobile in the search results and then click Select.
-
On the "App information" page, complete any other sections as needed and then click Next.
-
On the "Assignments" page, assign the Duo Mobile app as needed and then click Next.
-
Review the settings for Duo Mobile and then click Create.
Configure Managed Duo Mobile
-
In the Azure portal, navigate to Intune → Apps → App configuration policies.
-
Click the Add button and select Managed devices.
-
Enter the following information on the "Basics" tab of the "Create app configuration policy" page:
Name Enter a descriptive name for the app configuration policy. Description Enter additional information about this new policy, if desired. Device Enrollment Type Select Managed Devices. Platform Select iOS/iPadOS. -
Click the Select app link next to "Targeted app".
-
In the "Associated App" search, find and choose Duo Mobile. Click OK to return to the "Basics" tab, and then click Next.
-
On the "Settings" tab, use the "Configuration settings format" drop-down to choose Enter XML data.
-
Return to your Intune with App Config management integration page in the Duo Admin Panel and copy the AppConfig XML provided in step 3.7. Paste this into the XML property list field within the Intune app configuration policy page.
-
Click Next after entering the information for the configuration settings.
-
On the "Assignment" tab, choose the Azure group or groups to which you would like to push Duo Mobile. We recommend starting with a test group. Click Next after selecting your target groups.
-
Verify the information on the "Review + Create" tab, and if correct then click Create.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
Verify iOS Device Information with Search
After you configure the connection between Intune and Duo you can verify that a given device's information is being pulled into Duo by searching for the device identifier from the Duo Admin Panel. See Search for Device Identifiers to learn how.
iOS Certificate Configuration
End of Life Information
New Intune iOS certificate deployment management integrations may no longer be created as of October 2021. Consider migrating your certificate-based iOS Intune integration to Intune with App Config. See the Duo Knowledge Base article Guide to updating Trusted Endpoints iOS integrations from certificates to AppConfig for more information about migrating your iOS certificate-based management integrations to App Config.
These instructions remain available for customers who created these integrations before October 2021 and may need to reconfigure them. Duo continues to support existing Intune iOS certificate deployments and will do so until the integration reaches end-of-life status in a future update.
Create the Intune Integration
- Log in to the Duo Admin Panel and navigate to Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Intune in the list of "Device Management Tools" and click the Add this integration selector.
- Choose Certs for iOS from the "Legacy" options, and then click the Add button.
The new Intune integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Keep the Duo Admin Panel open in your browser while you access the Azure portal in a new window or tab. You'll need to return to the Intune management integration page to complete the iOS configuration steps.
Create the Duo Root Certificate Profile
-
Download the Duo Endpoint Root Certificate from the iOS tab of the Intune management integration page in the Duo Admin Panel.
-
In the Azure portal "Manage devices" section, navigate to Intune → Device → Configuration.
-
Click + Create → + New policy and make these selections on the "Create a profile" blade:
- Platform: select iOS/iPadOS
- Profile: select Templates → Trusted Certificate.
Click Create.
-
Enter this information in the "Trusted Certificate" profile editor:
- Name: provide a name for the Duo Trusted Root Certificate profile.
- Description: optionally add a description.
Click Next.
-
Upload the Duo Endpoint Root Certificate you downloaded earlier and click Next.
-
On the "Assignments" tab, assign the profile to your desired Azure users, groups, or devices. Click Next.
-
Verify the information on the "Review + Create" tab, and click Create if it looks correct.
Create the SCEP Certificate Profile
-
In the Azure portal "Manage devices" section, navigate to Intune → Device → Configuration.
-
Click + Create profile → New policy and make these selections on the "Create a profile" blade:
- Platform: select iOS/iPadOS
- Profile: select Templates → SCEP Certificate.
Click Create.
-
Enter this information in the "SCEP Certificate" profile editor:
- Certificate Type: select User
- Subject Name Format: enter CN=Duo Sandbox Endpoint Validation Issuing CA 2.
- Subject alternative name: select Email Address from the drop-down then set value as {EmailAddress}, and then also select User Principal Name (UPN) from the drop-down then set value as {UserPrincipalName}.
- Certificate Validity Period: select Years and enter 1.
- Key Usage: select Digital Signature.
- Key Size (bits): select 2048.
- Root Certificate: Click the + Root certificate link, select the Duo Root Certificate Profile you created in the previous config section, and click OK to make the certificate selection.
- Extended Key Usage: click the drop-down arrow under Predefined values and select Client Authentication (1.3.6.1.5.5.7.3.2) from the list. The "Name" and "Object identifier" values will be automatically filled.
- Renewal Threshold (%): Leave 20.
- SCEP Server URLs: Paste in the SCEP Server URL from the "Create the SCEP Certificate Profile" section of the iOS Intune management integration page you created in the Duo Admin Panel.
Click Next.
-
On the "Assignments" tab, assign the profile to your desired Azure users, groups, or devices, in the same way you deploy device profiles for other purposes. When making your assignment selections, consider the following:
- The SCEP certificate profile installs only on devices that run the platform you specified when you created the certificate profile, in this case iOS and iPadOS.
- You can assign certificate profiles to user collections or to device collections.
- To publish a certificate to a device quickly after the device enrolls, assign the certificate profile to a user group rather than to a device group. If you assign to a device group, a full device registration is required before the device receives policies.
Click Next after selecting the policy assignment targets.
-
Verify the information on the "Review + Create" tab, and click Create if it looks correct.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
Windows Configuration
This integration relies on having Duo Desktop present on your Intune-managed Windows endpoints. When users authenticate to applications protected with Duo's browser-based prompt, Duo matches the device information reported by Duo Desktop with managed device information obtained from Intune via API.
Use the following instructions to complete setup of your Intune with Duo Desktop management integration for Windows devices.
Create the Intune with Duo Desktop Integration
- Log in to the Duo Admin Panel and navigate to Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Intune in the list of "Device Management Tools" and click the Add this integration selector.
- Choose Windows from the "Recommended" options, and then click the Add button.
The new Intune with Duo Desktop integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Please note that this integration requires Duo Desktop to be installed on the device to be considered trusted.
Keep the Duo Admin Panel open in your browser. You'll need to refer back to the Intune with Duo Desktop management integration page to complete the configuration steps.
Register Azure Application for Windows in Duo
-
In the Azure portal, navigate to Microsoft Entra ID → App Registrations, and then select the Duo app registration you created earlier.
-
Scroll down on the configuration page for your Intune Trusted Endpoints management integration to the "Register Azure Application with Duo" section.
-
Copy the Azure application client secret value that you created during the Azure configuration steps, and paste the copied secret as the Azure Secret value in the third step on your Intune management integration's config page in the Duo Admin Panel.
-
Click Overview on the Duo Azure app registration's page. You'll see the Application (client) ID and Directory (tenant) ID listed at the top of the page.
-
Copy the Application (client) ID value from Azure and paste it as the Azure Application ID value in step 4 on your Intune management integration's config page in the Duo Admin Panel.
-
Copy the Directory (tenant) ID value from Azure and paste it as the Azure Directory ID value in step 4 on your Intune management integration's config page in the Duo Admin Panel.
-
Click Test Configuration to verify Azure API access, and if successful click Save & Configure on the Intune with Duo Desktop management integration page.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
Verify Windows Device Information with Search
After you configure the connection between Intune and Duo you can verify that a given device's information is being pulled into Duo by searching for the device identifier from the Duo Admin Panel. See Search for Device Identifiers to learn how.
Windows Certificate Configuration
End of Life Information
New Intune certificate deployment management integrations may no longer be created as of December 2021. Consider migrating your certificate-based Windows Intune integration to Intune with Duo Desktop. See the Duo Knowledge Base article How do I migrate from Duo Trusted Endpoints certificates to Trusted Endpoints with the Duo Desktop Application? for guidance that you may find useful in migrating Intune certificate-based management integrations to Duo Desktop.
Use of the Duo Desktop for trust attestation provides several advantages over the use of device certificates:
- It provides a more accurate assessment of your managed devices, and removes concerns about long-lived certificates present on devices no longer managed by your organization.
- It extends support to Firefox users. Trusted Endpoint certificate detection only works with Chrome, Edge, Safari, and Internet Explorer (depending on the management system).
- Improves trust detection for web browsers and thick client applications.
These instructions remain available for customers who created these integrations before December 2021 and may need to reconfigure them. Duo continues to support existing Intune Windows certificate deployments and will do so until the integration reaches end-of-life status in a future update.
Duo verifies the trusted status of Windows devices by checking for the presence of a Duo device certificate. You'll use Intune to push the Duo CA information to your Windows devices so they can obtain a Duo certificate.
Create the Intune Integration
- Log in to the Duo Admin Panel and navigate to Trusted Endpoints.
- If this is your first management integration, click the Get started button at the bottom of the Trusted Endpoints introduction page. If you're adding another management integration, click the Add Integration button you see at the top of the page instead.
- On the "Add Management Tools Integration" page, locate Intune in the list of "Device Management Tools" and click the Add this integration selector.
- Choose Certs for Windows from the "Legacy" options, and then click the Add button.
The new Intune integration is created in the "Disabled" state. You'll turn it on when you're ready to apply your Duo trusted endpoints policy.
Keep the Duo Admin Panel open in your browser while you access the Azure portal in a new window or tab. You'll need to return to the Intune management integration page to complete the Windows configuration steps.
Create the Duo Root Certificate Profile
-
Download the Duo Endpoint Root Certificate from the Windows tab of the Intune management integration page in the Duo Admin Panel.
-
In the Azure portal, navigate to Intune → Device → Configuration → Policies.
-
Click Create profile and make these selections on the "Create a profile" blade:
- Platform: select Windows 8.1 and later
- Profile: select Trusted Certificate.
Click Create.
-
Enter this information in the "Trusted Certificate" profile editor:
- Name: provide a name for the Duo Trusted Root Certificate profile.
- Description: optionally add a description.
Click Next.
-
Upload the Duo Endpoint Root Certificate you downloaded earlier, leave the "Destination Store" set to Computer certificate store - Root, and click Next, and then click Next again without adding any scope tags.
-
On the "Assignments" tab, assign the profile to your desired Azure users, groups, or devices. Click Next.
-
Verify the information on the "Review + Create" tab, and click Create if it looks correct.
Create the SCEP Certificate Profile
-
In the Azure portal, navigate to Intune → Device → Configuration → Policies.
-
Click Create profile and make these selections on the "Create a profile" blade:
- Platform: select Windows 8.1 and later
- Profile: select SCEP Certificate.
Click Create.
-
Enter this information in the "SCEP Certificate" profile editor:
- Name: provide a name for the Duo SCEP Certificate profile.
- Description: optionally add a description.
Click Next.
-
Enter the following configuration information Create a new profile with the values below.
- Certificate Type: select User.
- Subject Name Format: enter CN=Duo Endpoint Validation Issuing CA 1.
- Subject Alternative Name: select Email Address from the drop-down then type in for the value, and then also select User Principal Name (UPN) from the drop-down then type in for that value (so you have both attributes listed before proceeding).
- Certificate Validity Period: select Years and enter 1.
- Key Storage Provider (KSP): select Enroll to Software KSP.
- Key Usage: select Digital Signature.
- Key Size (bits): select 2048.
- Hash algorithm: select SHA-2.
- Root Certificate: Click the + Root certificate link, select the Duo Root Certificate Profile you created in the previous config section, and click OK to make the certificate selection.
- Extended Key Usage: click the drop-down arrow under Predefined values and select Client Authentication (1.3.6.1.5.5.7.3.2) from the list. The "Name" and "Object Identifier" values will be automatically filled.
- Renewal Threshold: enter 20.
- SCEP Server URL: Paste in the SCEP Server URL from the "Create the SCEP Certificate Profile" section of the Windows configuration tab on the Intune management integration page in the Duo Admin Panel.
Click Next, and then click Next again without adding any scope tags.
-
On the "Assignments" tab, assign the profile to your desired Azure users, groups, or devices, in the same way you deploy device profiles for other purposes. When making your assignment selections, consider the following:
- The SCEP certificate profile installs only on devices that run the platform you specified when you created the certificate profile, in this case Windows 8.1 and later.
- You can assign certificate profiles to user collections or to device collections.
- To publish a certificate to a device quickly after the device enrolls, assign the certificate profile to a user group rather than to a device group. If you assign to a device group, a full device registration is required before the device receives policies.
Click Next after selecting the policy assignment targets.
-
Verify the information on the "Review + Create" tab, and click Create if it looks correct.
Upload the PowerShell Script to Update Registry Settings
The PowerShell script configures automatic selection of the Duo certificate by Internet Explorer, and by Edge Chromium and Chrome as long as those browsers are installed on the client before the script runs. If Chrome or Edge Chromium get installed on the client afterwards, you'll need to make sure the PowerShell script runs on those clients again after installation to configure automatic Duo certificate selection.
-
Download the Duo PowerShell Script from the Windows tab of the Intune management integration page in the Duo Admin Panel.
-
In the Azure Portal, navigate to Intune → Device → Scripts and remediations → Platform scripts, and click Add.
-
Enter a Name for the script and a Description, if desired. Click Next.
-
Enter the following information on the "Script settings" page:
- Script Location: upload the Duo PowerShell script you downloaded from the Duo Admin Panel.
- Run this script using the logged on credentials: select No.
- Enforce script signature check: select No.
- Run script in 64 bit PowerShell Host: select No.
Click Next.
-
On the "Assignments" tab, assign the profile to your desired Azure users, or the users receiving a Trusted Endpoint Configuration from Intune. Click Next.
-
Verify the information on the "Review + Create" tab, and click Create if it looks correct.
At this point the configured integration is disabled and applies to no users until you finish your deployment.
Finish Trusted Endpoints Deployment
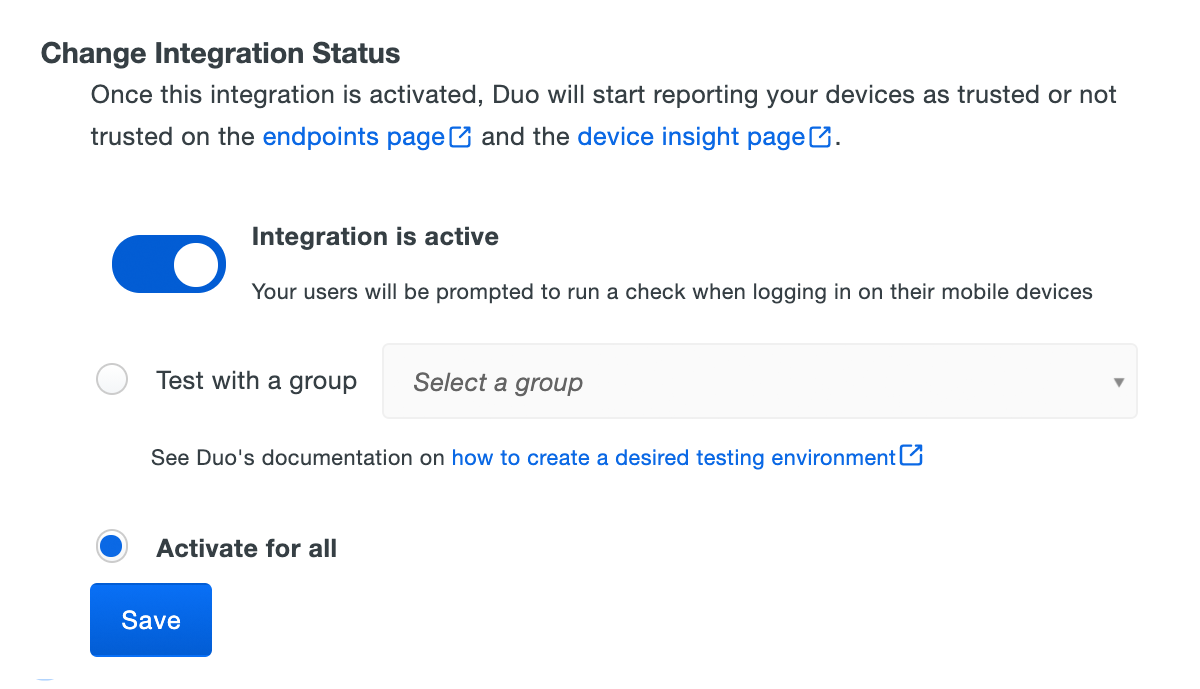
After creating the Duo Mobile management integration, set the Trusted Endpoints policy to start checking for managed device status as users authenticate to Duo-protected services and applications.
When your trusted endpoints policy is applied to your Duo applications, return to the Intune, Intune with App Config, or Intune with Duo Desktop trusted endpoint management integration in the Admin Panel. The "Change Integration Status" section of the page shows the current integration status (disabled by default after creation). You can choose to either activate this management integration only for members of a specified test group, or activate for all users. If you created more than one Intune management integration, you must activate each one individually.
The Device Insight and Endpoints pages in the Duo Admin Panel show which access devices are trusted/managed and enrolled in Duo Mobile.
Verify Your Setup
iOS App Config and Android
Users with Duo Mobile installed and activated for Duo Push on Android and iOS devices see a device trust dialog when authenticating to a protected resource via the Duo Prompt.
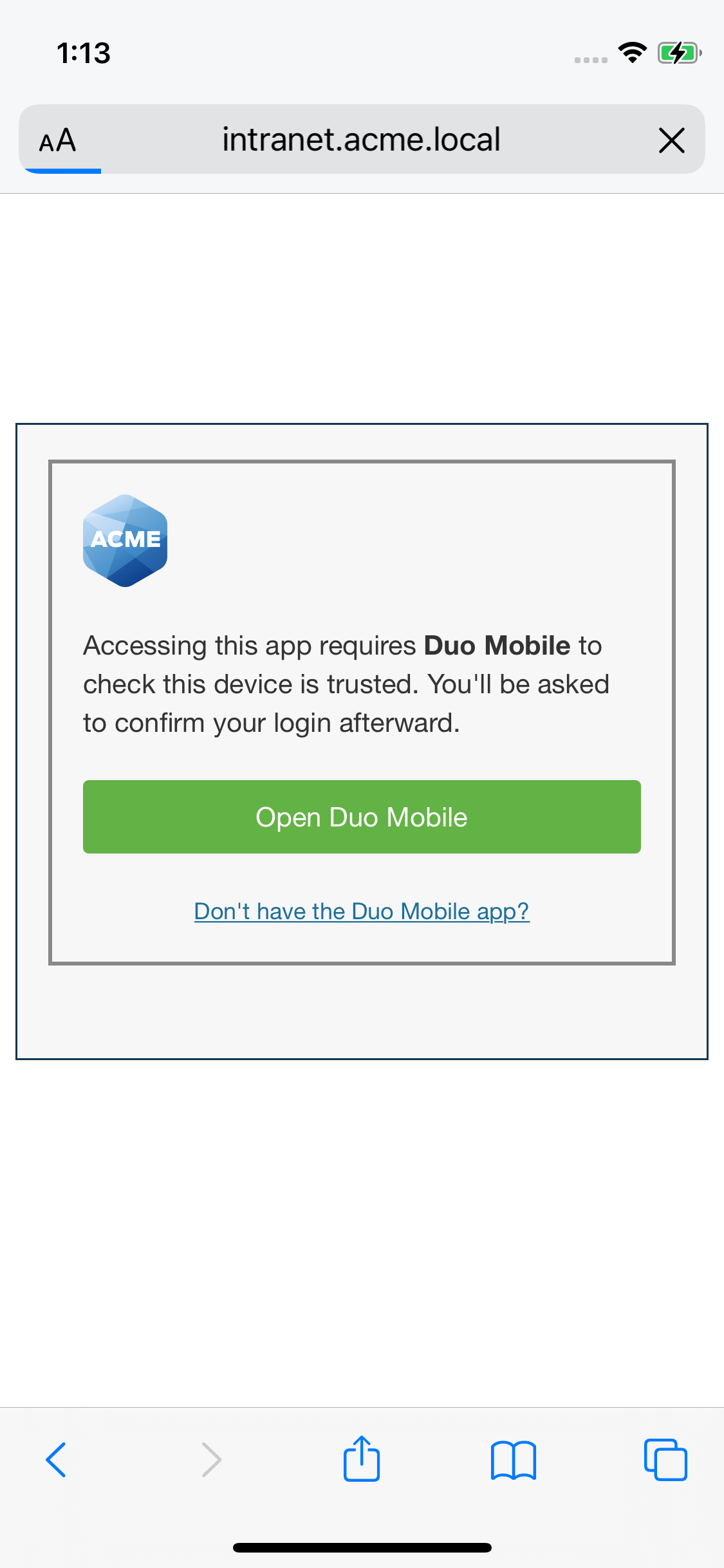
Duo uses the Azure application you created to perform a permissions check to verify device information.
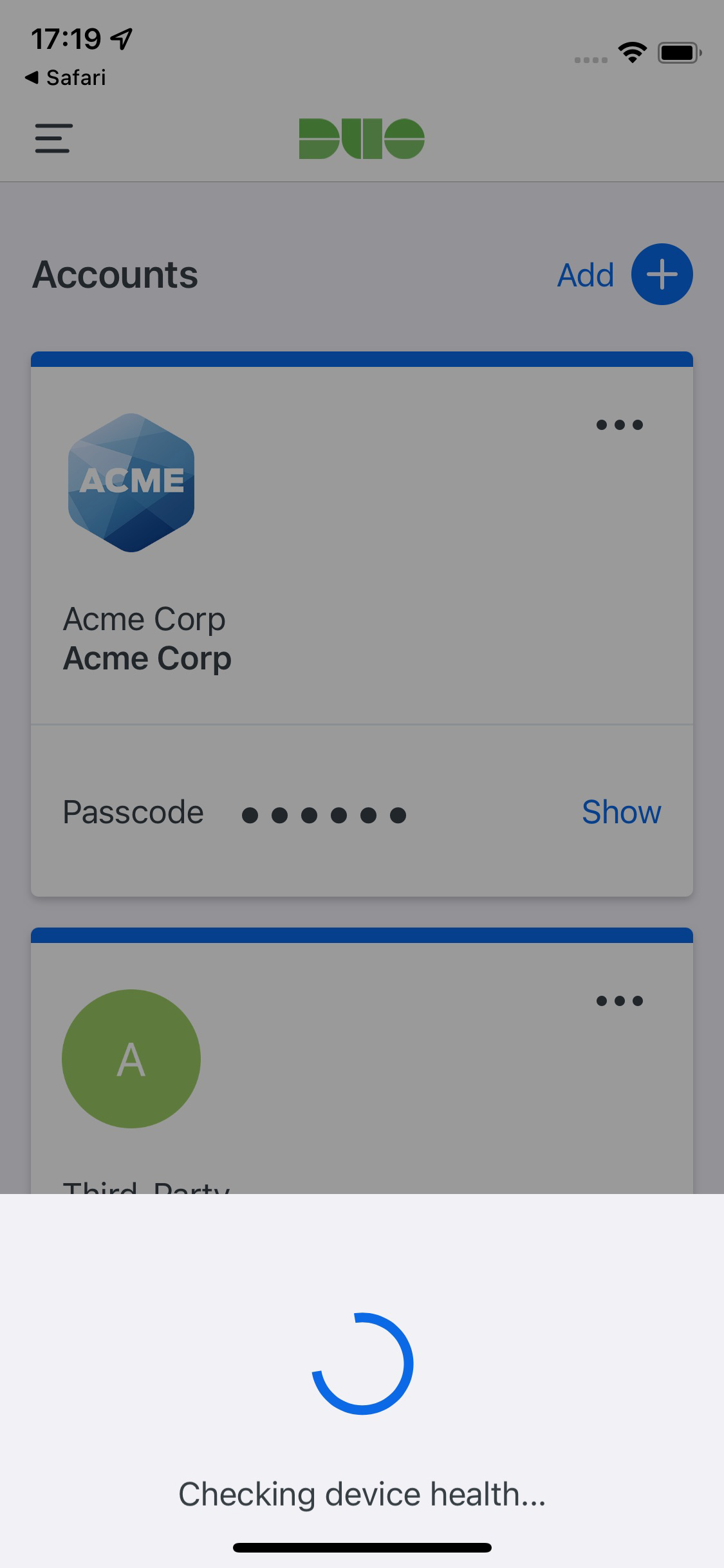
If Duo successfully verifies the Intune device information, and the user has Duo Mobile activated for Duo Push, then the user receives a login request on their phone.

On Android devices, approving the request grants access and returns the user to the protected application. On iOS devices, after approving the Duo authentication request users tap the top-left of the Duo Mobile app to return to the application and complete login. The "Second Factor" logged for these approvals is shown as "Duo Mobile Inline Auth" in the Duo authentication log.

If the user does not have Duo Mobile activated for push, or does not approve the Duo request before it times out, the user returns to the Duo Prompt, where they may select from the available factors to complete 2FA.
Windows with Duo Desktop
When Windows users access Duo-protected resources, the installed Duo Desktop provides device information to Duo. If the information from the device matches the information in Azure, Duo grants access to the trusted device.
iOS and Windows with Certificates
With the legacy iOS certificate configuration, iOS users will see a prompt asking them to choose a certificate when authenticating to a protected resource via the Duo prompt. After selecting the Duo Device Authentication certificate and completing authentication, subsequent Duo authentications from the same device will automatically use that same certificate for verification.
Legacy Windows certificate configuration users will see a prompt asking them to choose a certificate when authenticating to a protected resource via the Duo prompt. After selecting the Duo Device Authentication certificate and completing authentication, subsequent Duo authentications from the same device will automatically use that same certificate for verification.
Expanding to Additional Client Platforms
You only need to perform the Azure app registration and configuration in Duo once. The same Azure app is used for Android, iOS, and Windows Intune clients. After completing the full setup for one client platform in Duo, you need only complete the OS-specific setup steps for additional client operating systems.
Saving the Azure application secret you created for future reuse in a secure password manager lets you use the same Azure AD application registered while setting up your first Intune trusted endpoints management integration for future Intune management integrations.
Removing Devices from Intune
If you need to remove a device from Intune so that Duo no longer recognizes it as a managed, trusted device, do not use the "Retire" action in Intune. Instead, delete the device from the Intune portal. If you "retire" the managed device in Intune instead of deleting the device, Duo continues to recognize the device as managed and permit a user to authenticate from that still trusted device. If you use the "Wipe" action that will also delete the device from Intune, and wipe the device as well.
Search for Device Identifiers
If you configured Duo Desktop for Windows or Duo Mobile for iOS with App Config or Android to determine device trust, you may want to search for specific device identifiers to verify that the identifier information for a given trusted device exists in Duo. This can be useful to verify a device you expect to be trusted was imported from Intune into Duo.
To search for a device identifier in Duo:
-
Log in to the Duo Admin Panel and navigate to Trusted Endpoints.
-
Locate the Intune, Intune with Duo Desktop, or Intune with App Config device management integration you want to search for a device identifier in the list and click on it to view its details.
-
In the Check if devices have synced section, enter the identifier for the device you want to check and click Search.
-
A message appears indicating if the device identifier was either found or not found. If the device identifier is not found, check your Intune API configuration and wait 24 hours.
Use these instructions to find the device identifier to search in Intune.
- Log in to the Microsoft Intune admin center, navigate to Devices → All Devices, and select a device to view.
- Under "Monitor", select Hardware.
- The "UUID" labeled "Intune Device ID" is the device identifier. Copy this value and use it to perform the search in Duo.
Removing the Intune Management Integration
Deleting a trusted endpoints management tool integration from the Duo Admin Panel immediately invalidates issued Duo device authentication certificates. Be sure to unassign your trusted endpoints policy from all applications or remove the "Trusted Endpoints" configuration item from your global policy before deleting an existing Intune integration from "Trusted Endpoints Configuration". You should also disable your Duo admin user in Intune.
Leaving the policy settings in place after deleting a management tools integration may inadvertently block user access to applications.
Troubleshooting
Need some help? Take a look at our Trusted Endpoints Knowledge Base articles or Community discussions. For further assistance, contact Support.
